17. May 2022 By Juan Carlos Peñafiel Suárez and Dr. Vanessa Stahl
Why validating computer systems is important and the advantages that come along with it
The path to successful digitalisation in the laboratory requires the use of IT systems.
While a large part of the documentation and data volume for manual process steps is kept on paper, an increased level of digitalisation also entails an increased volume of data. This makes it all the more important to ensure that the IT systems that are used are validated so that the data that’s generated and processed is subject to the required quality criteria.
In this blog post, we’d like to explain why computer system validation (CSV) is of such key importance in the laboratory and which serious content-related and economic issues it is important to avoid.
The importance of CSV
If you consider the definition of the term ‘computer system validation’, the importance of carrying it out becomes clear. CSV is a documented process that consistently and reproducibly ensures that a computer system does exactly what it was designed to do. This means checking the system requirements as well as the stakeholder requirements and verifying the intended purpose. While the system requirements describe what the computer-assisted system must be able to do, the stakeholder requirements define the user requirements for the system itself. If only the fulfilment of the system requirements was verified, this would constitute verification. Therefore, checking both types of requirements is unavoidable if you wish to successfully validate a computer system.
High demands are placed on computer-assisted systems, especially in the pharmaceutical industry. The challenges here lie in the growing complexity of the data systems used in laboratories and the increasing focus on data integrity.
A computer-assisted system is deployed once the computer system validation that was carried out has been approved. The prerequisite for this is that compliance with the regulations specified in the pharmaceutical industry is verified by the authorities. The Food and Drug Administration’s (FDA) warning letters provide detailed insight into which mistakes should be avoided.
The source of mistakes
The FDA constantly audits every company that’s supposed to work under FDA regulations. The FDA makes the results of these audits available to the public – so they’re very open about them. Anyone with access to the Internet can view the warning letters.
You can use these letters to gain valuable information as to what mistakes companies have made in a given area, including CSV. The warning letters not only contain information about what the companies had failed to observe, but also about the corrective actions that the company should have taken at relatively short notice so that the mistakes detected wouldn’t be ‘displayed’. If the corrective actions aren’t good enough for the FDA, a report is written and ultimately published for public access as a warning letter. In every case, publishing this information puts an added amount of pressure on companies to correct these mistakes. This is a situation that every company wants to avoid. This is because not only are the company’s mistakes made known to their competition, but the company’s reputation is often damaged, which entails economic consequences. In addition, the company can’t continue to manufacture the products that are affected by the mistakes, making the damage even greater.
The most common mistakes
An analysis of several FDA warning letters shows that there are some mistakes in the field of computer system validation that are often repeated. These include:
- Having no backups available
- Having no access restrictions for computer systems
- Neglecting to use a software’s capabilities to store data
- Having only incomplete documentation or records
- Not protecting data, which means it can be deleted or changed by anyone
- Having no user accounts available
- Using unvalidated spreadsheets
Getting help is recommended, and often necessary
There’s nothing nice about a company getting a warning letter, because pressure from the public and the ongoing economic damage don’t really help to correct the mistakes, especially when it comes to computer system validation. An analysis of the system is usually needed to find out which solutions are best. Next, implementing such solutions requires time and money. To do this quickly and effectively, companies are often advised to seek help from professionals who have experience in this area and can look at the situation from a fresh angle. This is the best solution in many cases, as additional resources, which can be approved after the final phase, are often needed for this work. A group of external professionals is available to assist the company for as long as they’re needed and no longer than necessary.
Regulatory requirements for a CSV
There are no clearly defined regulatory requirements for a CSV, only very generally formulated requirements. This makes sense because, given that technology is constantly evolving, clearly defined regulatory requirements would have to be updated on a regular basis. Furthermore, the processes and computer systems that need to be validated are so complex that it’s almost impossible to find or prescribe standard solutions.
Important documents that should be considered for a CSV include:
- FDA 21 CFR (Code of Federal Regulations) Part 210
- FDA 21 CFR Part 211
- FDA 21 CFR Part 11
- EU GMP Annex 11
- GAMP 5 (Good Automated Manufacturing Practices)
Because the solutions aren’t prescribed, companies can find the appropriate solutions for their CSV themselves. This frees up a lot of extra room in which creativity, knowledge, technology and documentation must be brought together in order to find the optimal solutions.
Tips for a CSV/how to avoid the most common mistakes
A well-thought-out plan
A CSV must be planned in advance. There are different models for doing so. One of the proven models is the V-model. In this model, one stage is completed before the next one begins. The subsequent stage depends very heavily on the content of the previous one. What’s important about the V-model is that almost half of all the stages (right side of the V-model) verify the first half (left side of the V-model). This provides for a systematic way of working. Whether a stage is successful always depends on the quality and success of the previous ones. This is why it’s worth taking the time to invest knowledge in each stage in order to increase the quality of their results.
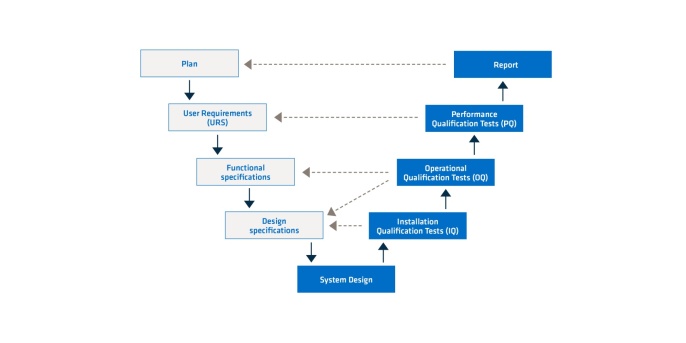
Figure 1. V-model for computer system validation.
Clear and precise user requirements
Only those who know the requirements of their own computer systems and processes are able to describe them well and know what should be tested in order to meet requirements. This also defines the scope of the CSV. Performing the validation requires a lot of resources, and they shouldn’t be consumed unnecessarily; that is to say, resources shouldn’t be involved in tasks that aren’t relevant to the requirements later on. Clear and precise requirements help to avoid this.
Constant communication with the Quality Assurance department
Computer systems are often complex. Data is generated which may still need to be evaluated. The processes supported by the computer systems should still be monitored. The documentation of these processes must be clear and accurate. These tasks are very time-consuming, which means staff can very rarely deal with a CSV on their own. This is why the Quality Assurance department exists. This department is in constant communication with the process managers and is constantly assessing the validity of the CSV and assisting with validation or re-validation in the process. Communication on both sides is crucial to keeping the Quality Assurance department well informed about the processes and the process managers well informed about the current CSV requirements.
Risk-based thinking
The very fact that the GAMP 5 document talks about a risk-based approach emphasises that this approach is important. Identifying risks is important because doing so makes it possible for measures to be taken which minimise the likelihood of these risks occurring. On top of that, not only can opportunities be strengthened, but improvements can be made as well. This is why a risk assessment is critical to the success of computer system validation. It’s also advisable not only to maintain documentation or methods in order to identify and assess risks, but also for a company’s personnel to develop this type of risk-based thinking. This makes it possible for everyone to contribute to identifying risks in future.
Conclusion
Nowadays, regulatory authorities require that computer system validation be carried out for the processes involved in producing medicinal products or medical devices. This validation enables companies to prove in writing that their computer systems work as expected. This isn’t just relevant to receiving an approval, it’s also relevant for the effectiveness of the process. A CSV helps to clearly define processes, minimise risks and increase opportunities. This means that the high expenditure on resources for validating the computer systems is an investment that will always pay off over the long term.
You can find more exciting topics from the adesso world in our blog articles published so far.


