28. August 2023 By Tobias Dieter and Domenic See
Cyber kill chain
A cyber kill chain is a framework developed to analyse and prevent cyber attacks. It provides a multi-tiered methodology for understanding, identifying and mitigating potential threats. The cyber kill chain is useful in understanding ransomware attacks or advanced persistent threats (APTs) and provides a clear description of the phases in the attack, allowing you to assess and adapt your network and system security.
There are many other models for describing cyber attacks, one example of this being the unified kill chain, which differ in terms of the level of detail they provide. adesso uses the cyber kill chain model primarily in seminars or as part of basic and advanced training courses, since the content is concise and can be easily conveyed.
The seven phases of the cyber kill chain
The cyber kill chain consists of a sequence of seven steps that correspond to the phases of a typical cyber attack. These steps are:
- Reconnaissance
- Weaponisation
- Delivery
- Exploitation
- Installation
- Command and control
- Actions on objectives
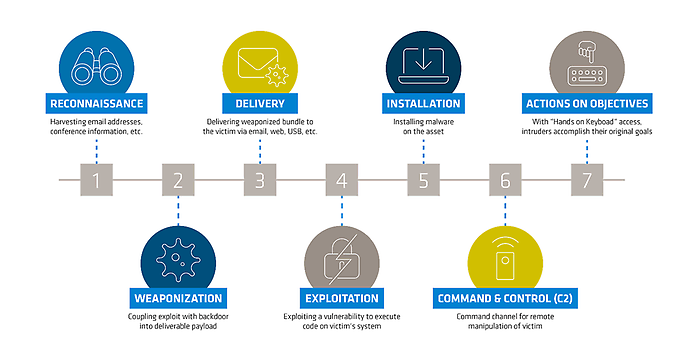
To establish effective prevention and response measures to cyber threats, it is important to understand each phase of the kill chain.
Reconnaissance
The first step in the cyber kill chain is reconnaissance, during which a hacker gathers information about their targets. This could include scanning for vulnerabilities, researching potential targets or collecting information on system weaknesses.
Weaponisation
The next step – weaponisation – involves using a suitable method of attack, such as an exploit or malware, to take advantage of the identified vulnerabilities.
Delivery
Once the ‘weapon’ has been created, it is delivered to the target in different ways. This is done, for example, via e-mail attachments, compromised websites or social engineering techniques.
Exploitation
This takes place when the target interacts with the tool sent to them that is used to carry out the attack (payload), allowing the hacker to gain unauthorised access.
Installation
Now having access to the victim’s system, backdoors, remote access tools or other malware are then installed on the system.
The installation phase can be highly critical for companies, since hackers take advantage of the opportunity to acquire long-term access to systems. These persistence measures could be, for example, processes or registry entries, to name two examples. In the case of a web server, web shells can be used, which allow the hacker to repeatedly gain access to the system.
These measures can also be carried out at the network level, where hackers can create Active Directory accounts in order to be active in the target object over the long term. The only option for a company subject to the cyber attack is to ‘reset’ the entire infrastructure, which proves to be a costly proposition. In some cases, the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, BSI) even recommends replacing all the hardware in the affected IT systems.
Command and control
Command and control refers to the next step where one or more hackers establish a communication channel with the compromised system that allows them to maintain control and issue commands remotely.
Actions on objectives
The hacker or hackers carry out their intended aims, which could range from stealing sensitive data to disrupting critical infrastructure.
Cyber kill chain as a proactive cyber defence strategy
Companies can use the cyber kill chain as a proactive defence strategy to effectively thwart cyber attacks. By understanding the different phases of a cyber attack, security teams are able to take preventive measures and appropriate countermeasures during each phase of the attack.
During the reconnaissance phase, for example, companies can monitor network traffic for suspicious activity or use threat intelligence tools to identify potential hackers. In the defensive phase, powerful e-mail filters and web gateways can help identify and block malicious payloads. In addition, the cyber kill chain can help when responding to the incident by providing a structured framework for investigating and mitigating cyber threats.
By analysing the lifecycle of the cyber attack, security analysts are able to identify the entry point for an attack, the techniques used and the targets of the hackers. This information is useful in formulating effective response strategies, minimising the impact of the breach and preventing future attacks.
Hackers are constantly improving their tactics, techniques and procedures (TTPs). Along with this, they are also are able to circumvent traditional cyber defences. For this reason, organisations should complement the cyber kill chain with other defensive mechanisms such as network segmentation, user training and continuous monitoring.
Indicators of compromise (IOC) and behavioural patterns are used detect and defend against attacks, which are based on known methods and frameworks such as the cyber kill chain, OWASP or MITRE ATT&CK. However, these indicators can lead to false alarms and flag legitimate activities as malicious. Conversely, hackers can use sophisticated techniques to bypass conventional IOCs, leading to false negatives. To minimise these risks, it is essential to regularly update threat intelligence sources and continuously upgrade detection mechanisms.
Conclusion
The cyber kill chain provides a structured and systematic approach to understanding and defending against cyber threats, leading to an overall improvement in security at the organisation. By breaking the lifecycle of the cyber attack into separate phases, companies have the opportunity to prioritise their defensive measures and allocate resources in an efficient way. In addition, the framework facilitates collaboration and communication between security teams, allowing them to share information, coordinate responses and identify gaps in cyber defences.
adesso offers extensive information and a wide array of courses on how to prevent, detect and respond to cyber attacks. Because the groups being targeted are so different, we offer services that provide personalised content for end users without any IT experience as well as for experts with special skills in the field.
Would you like to learn more about our services? Then feel free to get in touch with us.
Would you like to learn more about exciting topics from the world of adesso? Then check out our latest blog posts.
Also interesting:


